We learned about the basics of cryptography in the first post. We then learned about the types of cryptography – symmetric and asymmetric (private and public key cryptography). Then we mixed both of them to get the hybrid aspect. As if this was not enough, intelligent minds mixed hashing into cryptography to produce digital signatures.
It’s time to learn about this new potion – Digital Signature. Before we delve into detail, we must understand what is hashing. Hashing is a method to ensure that the integrity of the message has not been compromised. A one-way hash function is used for creating a hash that takes a variable-length string (a message) and produces a fixed-length value called a hash value. This hash value will only change if a change has occurred in the message. If there is no change, then the hash value will not change if you apply the one-way hash function 1 time or 1000 times. Let’s take an example to understand this.
Message: This blog really helps me to understand information security concepts in a simple manner.
There are various hashing algorithms that can be used to create a hash value for this message. For simplicity purposes, let’s consider the hash value after the hash function is: D34mCd768218g367.
What to do with value now? This value will help you identify if the message sent across has changed or not. How? If the message will change, the hash value will also change. This is just one piece of the puzzle of the digital signature.
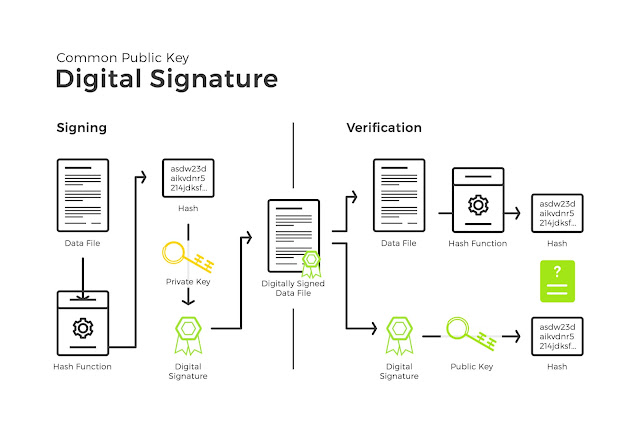
This diagram will help us to understand the complete picture.
Our old friends – Alice and Bob want to share information as usual. This time, however, an important requirement is that the message must not be modified. Alice, therefore, decides to use the digital signature to give confirmation to Bob that the message which he will get to read has not been modified.
These steps will help you understand the complete process.
- Alice has a data file with her. This is the secret script of Captain Marvel.
- She applies a hash function on this data file to create a hash value. This hash value will act as proof that no changes have been made in the script.
- This hash value is then encrypted to keep it safe. Alice uses her own private key for this encryption.
- This complete package is the digital signature.
- An important point to note here is that the data file is not encrypted here. The hash value is encrypted here.
- This digital signature is then appended to the data file and sent across.
- Bob receives this message and opens the data file.
- He is elated to see the Marvel script, however, he is unsure whether the message has been tampered with or not.
- To do that, he checks the public key of Alice and uses that to decrypt the hash value.
- In addition to that, Bob calculates the hash value of the message himself.
- Both these values are then compared by Bob to come to a conclusion about whether the message’s integrity has been tampered with or not.
The hashing function ensures the integrity of the message, and the signing of the hash value provides authentication and non-repudiation. The act of signing just means the value was encrypted with a private key.
It would be extremely unfair if I leave you without questions to tax your brain. Do not forget to leave answers to them in the comment(s) section below.
1. What would be the best key for the digital signature – Private or Public?
2. If the hash value is different, does it mean that the digital signature is corrupted?
3. Do digital signatures provide non-repudiation?



Comments ()