How many of you have applied proxy for one of your friends during the attendance call in the class? If I assume, it’s a yes from everyone, you will have no difficulty in understanding this one. A Proxy is someone who is acting on your behalf and acting as the middleman. We take a more detailed example in some time to clearly understand this.
A proxy firewall stands between a trusted and untrusted network and makes the connection, each way, on behalf of the source. When you as a user, will send a request to, say connect, to www.facebook.com, the request will go through the proxy firewall to check what request has been made. The proxy firewall will stop your connection, initiate a new connection on your behalf, and wait for the incoming traffic. Surely, it finds that you have requested a website that is quite known for leaking personal data, it stops the traffic and sends you a message that this website cannot be connected to. This is unlike the packet filtering firewall. Where a packet filtering device just monitors traffic as it is traversing a network connection, a proxy ends the communication session and restarts it on behalf of the sending system.
To better understand this concept, let’s take an example. If you have seen the various Bond movies, you know that the CIA sends him to do their dirty work. In a hostage situation, Bond acts as a middleman and fights with the bad guy. The CIA chief just enjoys the show from his office. You can call the proxy firewall as the Bond. It takes your request, acts on your behalf, sends the request as if it was coming from it, and then checks the data received, and, if and only if it considers the data safe, transfers it to you. A bubbling hot question comes to my mind – How does the middleman do it?
Now a proxy technology can actually work at different layers of a network stack. A proxy-based firewall that works at the lower layers of the OSI model is referred to as a circuit-level proxy. A proxy-based firewall that works at the application layer is called an application-level proxy. It’s just like James Bond and Ethan Hunt!!!
Before we go into their differences, let’s focus on high-level functioning.
You are the Real Client here. You send a request to access a website. A proxy firewall has been deployed in your organization. So your request goes to the proxy server which can or cannot be a part of the firewall. The proxy will accept your request and start analyzing it. There are many cases where rules are built in within the proxy server to terminate your request if your request violates a rule. Trying to access a pornographic website will be blocked if the rule is configured. This is not mandatory, but, over time, companies do blacklist certain URLs which are deemed unsafe. This also reduces the pressure on the firewall to service every request.
If your request is accepted, the proxy will send a similar request on your behalf to the internet. The web server responds to the HTTP request from the proxy server, unaware the request is coming from a user behind a proxy. After analysis, it sends the request back to you, so that you can start wasting your time on Facebook.
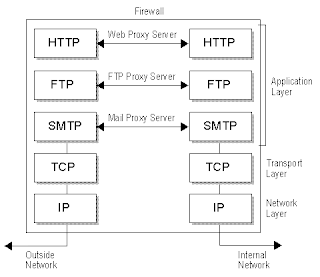
The devil lies in the details and it’s time to know the details. There are 7 layers in the OSI model and you can remember them – Please Do Not Throw Sausage Pizza Away for Physical, Datalink, Network, Transport, Session, Presentation, and Application layers. A circuit-level proxy works at the session layer of the OSI model and monitors traffic from a network-based view. This type of proxy cannot “look into” the contents of a packet; thus, it does not carry out deep-packet inspection. It can only make access decisions based on the protocol header and session information that is available to it. Sounds familiar like the packet filtering firewall. It is, but the difference here lies in the fact that it acts as a proxy on your behalf. Application-level proxies work at the application layer and understand the packet as a whole and can make access decisions based on the content of the packets. They understand various services and protocols and the commands that are used by them.
The application layer comprises of various protocols such as HTTP, HTTPS, Telnet, FTP, SMTP, etc. An application proxy will comprise separate proxies for screening the data to be deemed safe. Does this mean that I have to buy different proxy firewalls for all these different applications? Not at all. If you are watching a show on Netflix, you can change the audio language to Hindi, Russian, or Chinese any time you want. In a similar manner, the proxy firewall remains the same, it’s just that one portion of the firewall product is dedicated to understanding how a specific protocol works and how to properly filter it for suspicious data.




Comments ()