Having learned about cryptography in the previous article, it is now time to learn about the types of cryptography. You are right, nothing is complete till we understand its types and subtypes and so on. Remember, your best friends, Alice and Bob!!! They are going to help us understand the types of cryptography.
Before we go into the details, we ought to recapitulate a few terms.
1. Plain text – Data in a readable or understandable format.
2. Ciphertext – Random and unreadable text
3. Encryption – Process of converting plain text into cipher text.
4. Key – Sequence of random bits
5. Algorithm – Rules by which encryption and decryption will take place.
It is really important to clearly understand these terms, else, the journey ahead will be difficult. So lets us begin.
Cryptography algorithms are either symmetric algorithms, which use symmetric keys (also called secret keys), or asymmetric algorithms, which use asymmetric keys (also called public and private keys). I know, this can be confusing, if you read this the first time, however, you’ll be able to sail through if you pay close attention.
If you and I share the same password, we are using the symmetric algorithm and if we use a public and a private password, we are using the asymmetric algorithm. This is not technically correct, however, explains it in a manner that you can understand.
Symmetric Algorithm
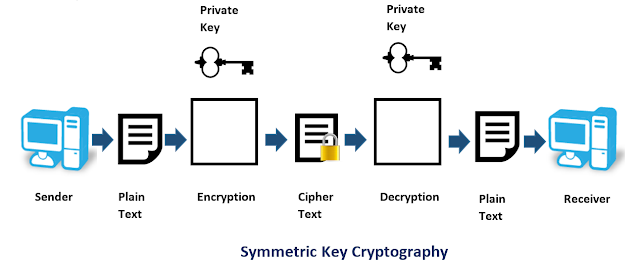
Alice and Bob, as usual, want to communicate with each other. Alice has an old-age secret recipe for pancakes which Bob has requested from Alice. Given the current scenario of data breaches happening everywhere, Alice is skeptical of sending it as such. She discusses this with Bob and they both decide to use symmetric cryptography for this purpose. In a cryptosystem that uses symmetric cryptography, the sender and receiver use two instances of the same key for encryption and decryption. This means that if Alice uses the key “123@encrypt” for encrypting, Bob will also use the same key to decrypt it. Each pair of users who want to exchange data using symmetric key encryption must have two instances of the same key.
The diagram below also illustrates the same.
Clearly, in symmetric encryption, it is the secrecy of the key that plays the most important role. If 3 people wish to communicate with each other, all 3 must have the same key, and most importantly, all 3 of them must keep it secret. Hence, keeping the key secret is a big task, if there are many people involved.
We learned that cryptography helps us achieve confidentiality. Symmetric cryptography can help us achieve that, but, can it help us achieve integrity, non-repudiation, or authentication? Think for a minute. What is integrity? No unauthorized modification. But if the secret key is no longer secret, you cannot be 100% sure that no modification has taken place. There is also no way to prove who sent the message if two or three people are using the same secret key.
Despite the above-mentioned shortcomings, symmetric key cryptography is quite fast and easy to implement without demanding many resources. Hence, it is used quite a lot, but, in collaboration, with asymmetric cryptography.
Asymmetric Cryptography
Just like every celebrity has a public life and a private one, asymmetric cryptography is just the same. Here we use 2 different keys, as if 1 was not enough, we brought two here!!! There is a public one and a private one and synonymous with the names, the public key is to be used in public and the private to be used only in private. One is used for encryption and the other one for decryption. They are also mathematically related.
I can see the look on your face. You are confused and want to give up. Absolutely No! Let’s simplify this monster through an example.
Alice and Bob want to again talk to each other. This time they have a big secret to share with each other. Alice has a secret copy of the script of the latest movie Avengers 4 and she wants only Bob to look at it. Alice and Bob live far away and it is impossible to share a secret key. So they use asymmetric cryptography. What happens here is, we use a mathematical function to derive a set of keys. However, if you have one key, you shall not be able to generate the other one. This means that if an evildoer gets a copy of Bob’s public key, it does not mean she can employ some mathematical magic and find out Bob’s private key. But if someone got Bob’s private key, then there is big trouble—no one other than the owner should have access to a private key.
An important point to note here is that either key from this set can act as a private or a public key and can be used for encryption or decryption. What Bob needs is to keep one of them extremely safe and the other one can be listed anywhere.
What really happens then? If Bob encrypts data with his private key, the receiver must have a copy of Bob’s public key to decrypt it. The receiver can decrypt Bob’s message and decide to reply to Bob in an encrypted form. All she needs to do is encrypt her reply with Bob’s public key, and then Bob can decrypt the message with his private key. It is not possible to encrypt and decrypt using the same key when using an asymmetric key encryption technology because, although mathematically related, the two keys are not the same key, as they are in symmetric cryptography.
Bob can encrypt data with his private key, and the receiver can then decrypt it with Bob’s public key. By decrypting the message with Bob’s public key, the receiver can be sure the message really came from Bob. A message can be decrypted with a public key only if the message was encrypted with the corresponding private key. This provides authentication because Bob is the only one who is supposed to have his private key. If the receiver wants to make sure Bob is the only one who can read her reply, she will encrypt the response with his public key. Only Bob will be able to decrypt the message because he is the only one who has the necessary private key.
Sounds confusing? Well, it is. However, if we read this, again and again, we’ll able to decipher it in some time. Bookmark this page now!!
Let’s try to summarize this:
1. Bob has a set of public and private keys.
2. Alice wants to send a message to Bob, so she searches for this public key.
3. She encrypts the data using this key, as it is publically available.
4. She also knows that only the person having the corresponding private will be able to open the message and no one else.
5. Bob uses his private key to decrypt the message.
6. He reads the story of Avengers 4 and is happy that all turns out well in the end!!!
Well, I know, you are tired and exhausted, but why not leave with you a set of questions to help you know how much of all this you understood? In the next article, we are going to mix both of these – symmetric and asymmetric and understand how we implement hybrid cryptography.
It would be great if you leave the answers to below questions in the comments section below:
1. If I encrypt the data with your private key, what would I achieve?
2. If I encrypt the message which I intend to send you with my private key, would that help me in implementing confidentiality?
3. Alice wants to send a message to Bob and prove that she has sent the message. Will, that work if she encrypts the message with her private key?
4. If a symmetric key is encrypted with a receiver’s public key, what security service(s) is provided?




Comments ()