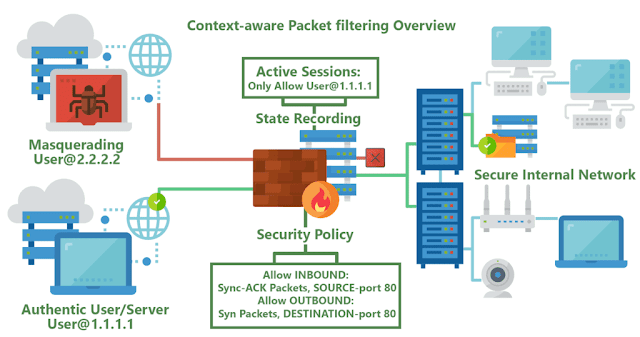
In continuation with our series on understanding firewalls, the next type is the stateful firewall. This one remembers and keeps track of what packets went where until each particular connection is closed.
To understand this, we need to take an example. If you watch a little bit of crime drama, you will find that in most cases the neighbor knows everything. He is spying day and night on you and others in the neighborhood. He knows that the man on the left side of the road deals in weed and goes out of the house at night, the construction guy who takes long breaks inside the garage, the milkman who smiles and pours extra milk looking at the handsome guy that lives next door and so on.
Most of the well-known protocols have a sequence of connecting. For eg – If you consider the TCP protocol which is a connection-oriented protocol, it goes through three steps before a connection is established. This is commonly known as the 3-way handshake. If my system wants to communicate with your system using TCP, it will send your system a packet and in the TCP header, the SYN flag value will be set to 1. This makes this packet an SYN packet. If your system accepts my connection request, it will send back a packet that has both the SYN and ACK flags within the packet header set to 1. This is an SYN/ACK packet. In addition to this, there are multiple other parameters that are finalized during this handshake.
Let’s take an example of a bureaucratic office setup to understand this concept. You need to take and deposit a job application form. The security guard at the reception area scans your government id and allows you to enter inside. You take the form from reception and fill it that. You are then asked to get it stamped from the superintendent’s office and finally submit it at the director general’s office. Let’s map your movements to the above example. Consider this security guard as the stateful firewall. I will explain the stateful part a little later. He is the firewall as he filters you on the basis of a government id card. Just like the TCP, you go to the reception to ask for the application form ( you initiate the handshake), after the form is handed over, you go for stamping ( syn/ack) and final submission means the ACK. In this case, you are considered a potential candidate and all your states – from getting the form to its final submission is also tracked closely by the guard. That’s why he is like the stateful firewall which tracks the complete cycle of the service. This is unlike the packet firewall where the guard would have just let you inside by verifying the government id and did not keep track of you.
So “keeping the state of a connection” means keeping a scorecard of all the various protocol header values as packets go back and forth between systems. The values not only have to be correct—they have to happen in the right sequence. For example, if a stateful firewall receives a packet that has all TCP flag values turned to 1, something malicious is taking place. Under no circumstances during a legitimate TCP connection should all of these values be turned on like this. Attackers send packets with all of these values turned to 1 with the hopes that the firewall does not understand or check these values and just forwards the packets to the target system. The target system will not know how to process a TCP packet with all header values set to 1 because it is against the protocol rules. The target system may freeze or reboot; thus, this is a type of DoS attack. Firewalls today understand such cases and respond accordingly by terminating such connections.
While TCP is a connection-oriented protocol where there are 3 steps that need to take place, UDP is a connectionless protocol. How would a stateful inspection firewall work in that case? For connectionless protocols, a stateful firewall keeps track of source and destination addresses, UDP header values, and some ACL rules. This connection information is also stored in the state table and tracked. Since the protocol does not have a specific tear-down stage, the firewall will just time out the connection after a period of inactivity and remove the data being kept pertaining to that connection from the state table. It’s similar to some banking websites which implement that in case of inactivity, you are logged out of the session. The stateful firewall keeps an eye on such UDP connections and in case it finds some trouble or inactivity, it times out the connection.


Comments ()