Bob heaved a sigh of relief after he saw the mail. The payment had been processed and he immediately received the payment confirmation from the vendor. It was the end of the month and he wanted no non-compliance on the part of his company toward paym...
Read More
While multiple modes of communication have mushroomed in the past few years, the good old-fashioned email remains the top means of communication for businesses. It also remains the top priority for all social engineers out there who come up with new ...
Read More
Your fingerprints help identify you uniquely. Your fingerprints are made of multiple lines that run in a fashion that is unique for every individual on this planet. A slight change in the fingerprint will result in altogether a new person. Well, hash...
Read More
“****, my system has been attacked by ransomware…” has been one of the most commonly said statements in this year alone… The last several months have seen ransomware evolve from a relatively small hacker operation into a global IT epidemic, and one o...
Read More
We learned about the one-way hash function in the previous blog post. We understood that a strong hashing algorithm does not produce the same hash value for two different messages. If the algorithm does produce the same value for two distin...
Read More
Block ciphers have several modes of operation and each mode works in a specific way. Each mode of operation has its own utility and performs well under specific circumstances. Sometimes you may find that there is a trade-off between security and conv...
Read More
In the previous blog post, we learned about the Electronic Code Book (ECB), Cipher Block Chaining (CBC), and Cipher Feedback (CFB) modes of operation. While the ECB mode has been made for very small blocks, the CBC mode works the best with large bloc...
Read More
Quite often in the world of cryptography will you hear the term, PKI or Public Key Infrastructure. While people often use this term loosely without understanding ( and even appreciating) the whole gamut which this word entails, it is extremely import...
Read More
In the previous blog post, we learned about the various pieces of the puzzle called the public key infrastructure. It’s time to learn how these pieces work after fitting together.The PKI is made up of the following different components.• Certificatio...
Read More
“Trust” is what was the starting point of the discussion on PKI. The public key infrastructure is based on the premise to enable trust between unknown parties to ensure the secure transmission of information. Another element that ensures trust is the...
Read More
In the previous blog post, we dissected the definition of cloud computing as per NIST and ISO/IEC. Before you proceed further, I urge you to read it before continuing. In this blog post, we will learn about traditional virtualization and how the clou...
Read More
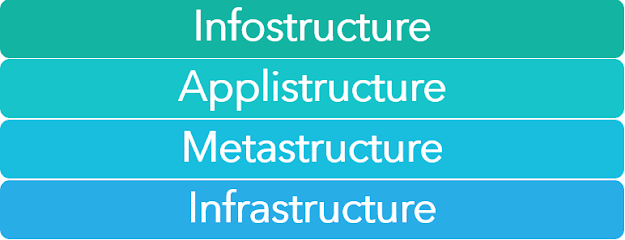
At a high level, both cloud and traditional computing adhere to a logical model that helps identify different layers based on functionality. The four layers are :Infrastructure: The core components of a computing system: are compute, networ...
Read More
When I was preparing for CISSP a few years back, a line from the book AIO guide - by Shon Harris really made an impact on me. It goes like this “ There are only two people in the world I trust - You and I and I m not so sure about you.” This statemen...
Read More
Governance and Risk management are some of the most important aspects of any business, irrespective of the fact whether you are running your applications (business) in the cloud / on-prem or even space. All businesses need to be governed and risks fa...
Read More
What if it is possible to analyze or manipulate encrypted data without revealing the data to anyone? Make an encrypted search query to a search engine and the results come back in an encrypted form, payment data is never decrypted, and still, transac...
Read More