A recent survey by Trend Micro revealed alarming results. When asked for feedback on companies’ approaches to cloud data destruction, 25% of the population responded with “What’s that?” as the response. Another 31% said their cloud provider handles c...
Read More
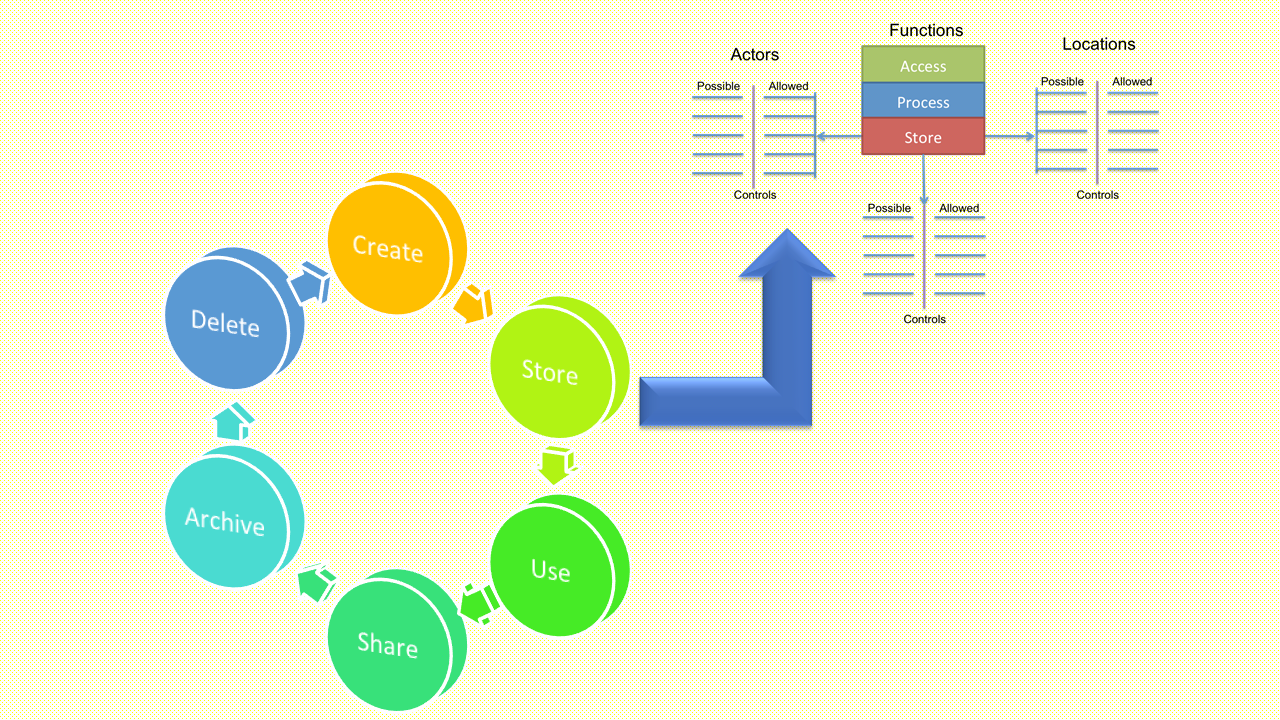
The Cloud Security Alliance Guidance explains the Data Security Lifecycle which mentions the various phases data undergoes in the cloud. This lifecycle was adapted from a blog article on Securosis. Rich Mogull, Analyst & CEO, stated that he was n...
Read More
“Horizon scanning is a technique for detecting early signs of potentially important developments through a systematic examination of potential threats and opportunities, with emphasis on new technology and its effects on the issue at hand.”With the w...
Read More
Well, we all love predictions, don’t we? The new year rings in and there is a flood of predictions from all ends - financial trends, fashion trends, puppy trends, climate trends, and whatnot!! How can cybersecurity be far behind? Google “Cybersecurit...
Read More
What does a typical workday in the life of a CISO look like? Most CISOs would agree that there are myriad things that are constantly begging for attention in their work, and yet have 20 extra things that land up in their inbox that need to be sorted ...
Read More
Consider you are a security expert employed by:1) A big entertainment company, OR2) Product Company, OR3) Manufacturing company. And you have been asked to create the security policy for the organization. How would you go about creating one? Whi...
Read More
Intriguing attack name isn’t it? Pronounced as TOCKTOO, this is a time-of-check/time-of-use (TOC/TOU) attack. This deals with the sequence of steps a system uses to complete a task. This type of attack takes advantage of the dependency on the timing ...
Read More
What comes to your mind when you think of information security? If you watch a lot of movies, especially the ones involving the CIA, you would imagine a nerd in a basement trying to hack into the world’s most secure places with no life other than tha...
Read More
How many customers are migrating to the cloud today? Well, mostly all of them. The reasons are multifold - cost-cutting, digital transformation, online presence, backups, etc. Companies are moving their entire enterprise data in a lot of cases entire...
Read More
Technologies and buzzwords come and go, but, in technology terms, some often make the cut and go into the big league. Think of cloud computing 20 years ago, or zero trust around 5 years ago. Today everyone is just gushing over it and calling it the n...
Read More