If you would like to send a letter to me, what would be the most important aspect for you to send it across? My address. If you would have observed, we usually write the address in a certain format – building number, followed by area, city, state, an...
Read More
We just love to mix things up. Well, yeah, and why not? When we get the best of both worlds, we can mix anything up. Even when it is so complex in itself like cryptography. In the last article, we learned about symmetric and asymmetric cryp...
Read More
Having learned about cryptography in the previous article, it is now time to learn about the types of cryptography. You are right, nothing is complete till we understand its types and subtypes and so on. Remember, your best friends, Alice a...
Read More
“ $%^*^* Nh%&gfg K97@#”. Well, I’m 100% sure that you did not understand what I meant to say through these words. This is what cryptography is all about. Nah, don’t think that if you are unable to read what was written, it becomes an impleme...
Read More
We learned about the basics of cryptography in the first post. We then learned about the types of cryptography – symmetric and asymmetric (private and public key cryptography). Then we mixed both of them to get the hybrid asp...
Read More
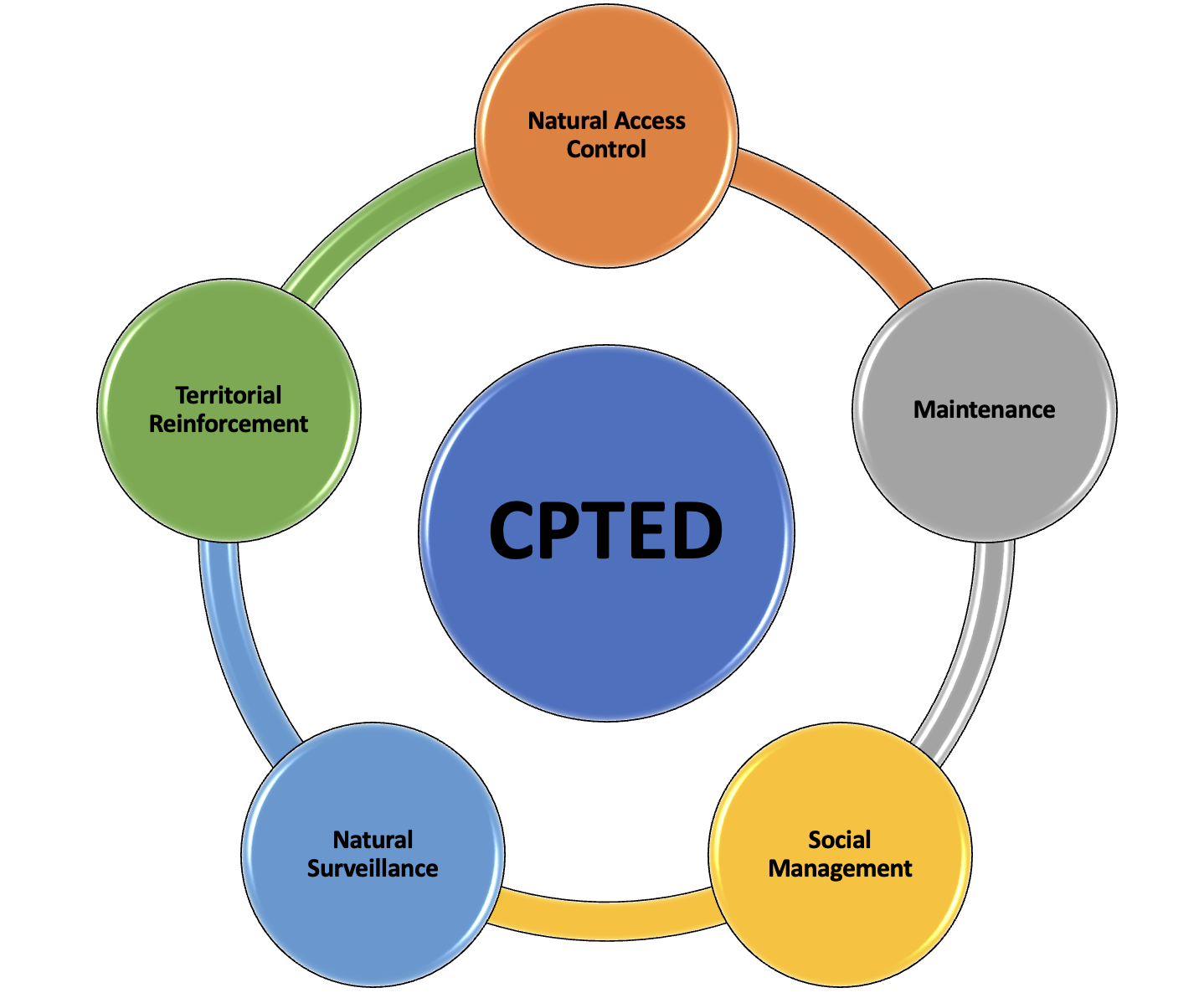
Security design and access control are more than bars on windows, a security guard booth, a camera, or a wall. Crime prevention involves the systematic integration of design, technology, and operation for the protection of three critical assets-peopl...
Read More
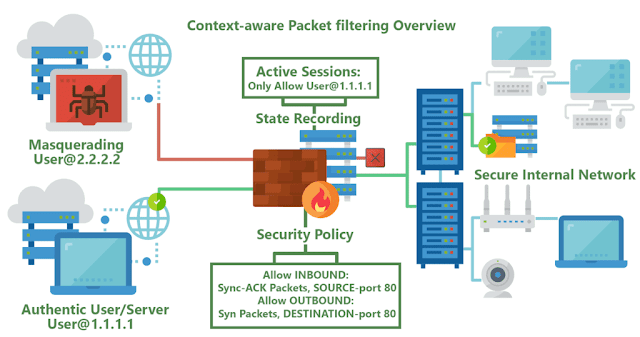
If you are hearing about the term firewall for the first time, and consider it as a wall on fire, you are at the right place. Because that is the overall idea behind this!!!A firewall is one of the most used terms in the field of information security...
Read More
In the earlier blog post on the basics of the firewall, we learned what exactly is a firewall and what does it do? It’s time to learn about the various types of firewalls and how they function. I will dedicate one post each to the types of ...
Read More
In continuation with our series on understanding firewalls, the next type is the stateful firewall. This one remembers and keeps track of what packets went where until each particular connection is closed.To understand this, we need to take an exampl...
Read More
How many of you have applied proxy for one of your friends during the attendance call in the class? If I assume, it’s a yes from everyone, you will have no difficulty in understanding this one. A Proxy is someone who is acting on your behalf and acti...
Read More
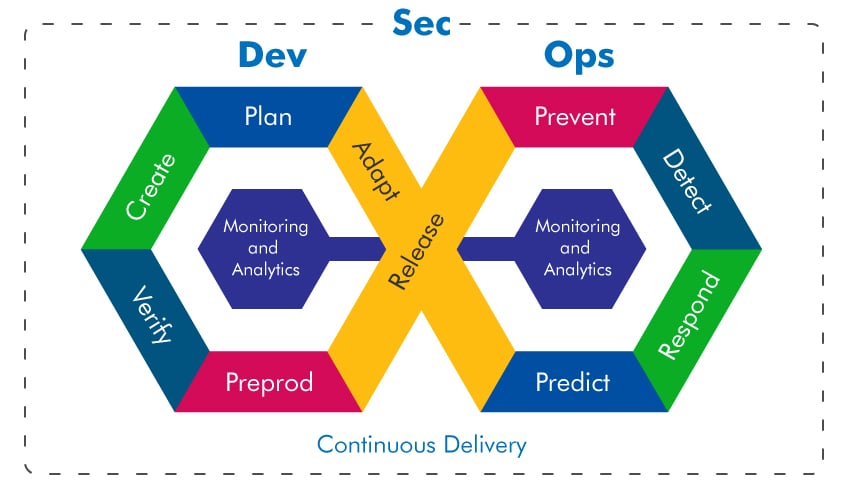
If you are even remotely associated with the security or the software development world, you would have heard the term - DevSecOps or just DevOps. If not, you are surely living under a rock!! DevOps is one of the hottest trends in the software develo...
Read More
Paul is flying on an airplane from Bangkok to Hawaii. While the air hostess serves him a glass of champagne, Paul enjoys the calmness of the clouds around him. His flight is about to land in another 20 minutes. The pilot is communicating with the air...
Read More
The Recipe is simple. Set up a network. Add a bit of internet to the mix. To improve the taste, add firewalls, IDS, IPS, and some monitoring programs. It's time to divide the network so that it can be served as per the requirements of the guests. Seg...
Read More
There's nothing more comforting than indulging in a slice of homemade cake paired with a piping hot cup of coffee or tea. Sounds rejuvenating, right? Take the flour, eggs to beat, powdered sugar, and a cup of milk. Follow the recipe and viola the cak...
Read More
Once upon a time, there were three little pigs. Over time, the little pigs educated themselves. They came back to meet their mother before they went ahead and opened their new companies. Mother told them " Whatever you do, do it the best that you can...
Read More